
Exposing Hidden Security Flaws
From my room — March 16, 2024
Hello World!,
So, recently I was curious and started reading the source code of an educational website I knew about, and the things I found, if anyone else had found them, would have cost the company a lot of money.
In this blog post I will be talking exactly about the things I found, why you shouldn't expose them, and how you can secure your system from these vulnerabilities.
1. What I found
While checking the minified code of the website, I randomly out of nowhere searched "REACT_" because I knew that the website was built using React, and in React API keys and secrets commonly used "REACT_APP" in the starting of the variable name, so I searched for it and found this.
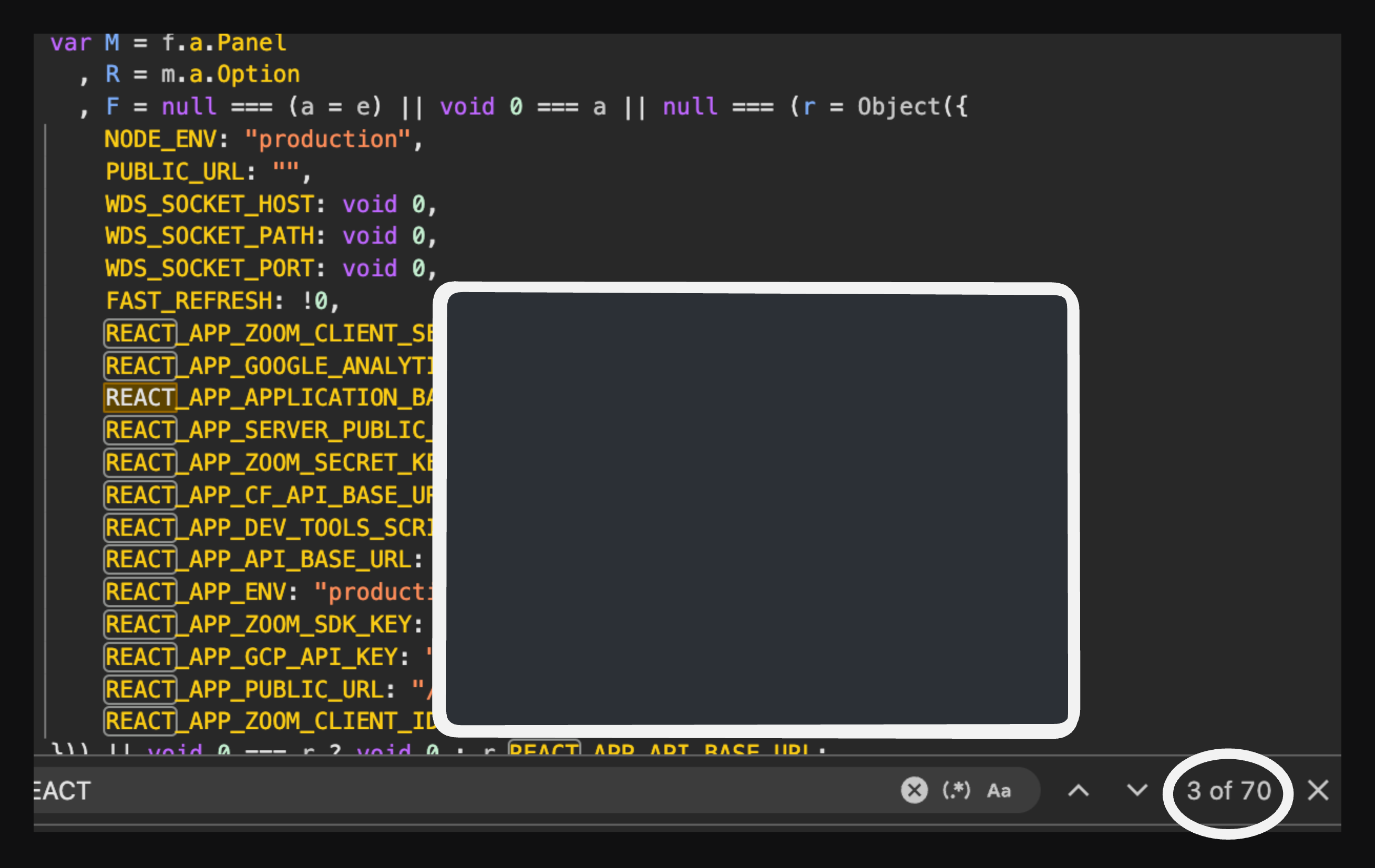
Environment Variables
And after finding this, my confidence and curiosity got the best of me, and I started digging deeper. I found that the website had 2 backend APIs and only had the URL exposed in the network tab; another one was "hidden" in the code that I obviously found, and after that I stopped and started installing Kali Linux because I wanted to dirbust the API, and after dirbusting it, I found that it had a URL /users/Cat—this was a GET URL without any authentication, so I opened it in my browser and found that it was leaking companies sensitive info and some data of around 10 employees.
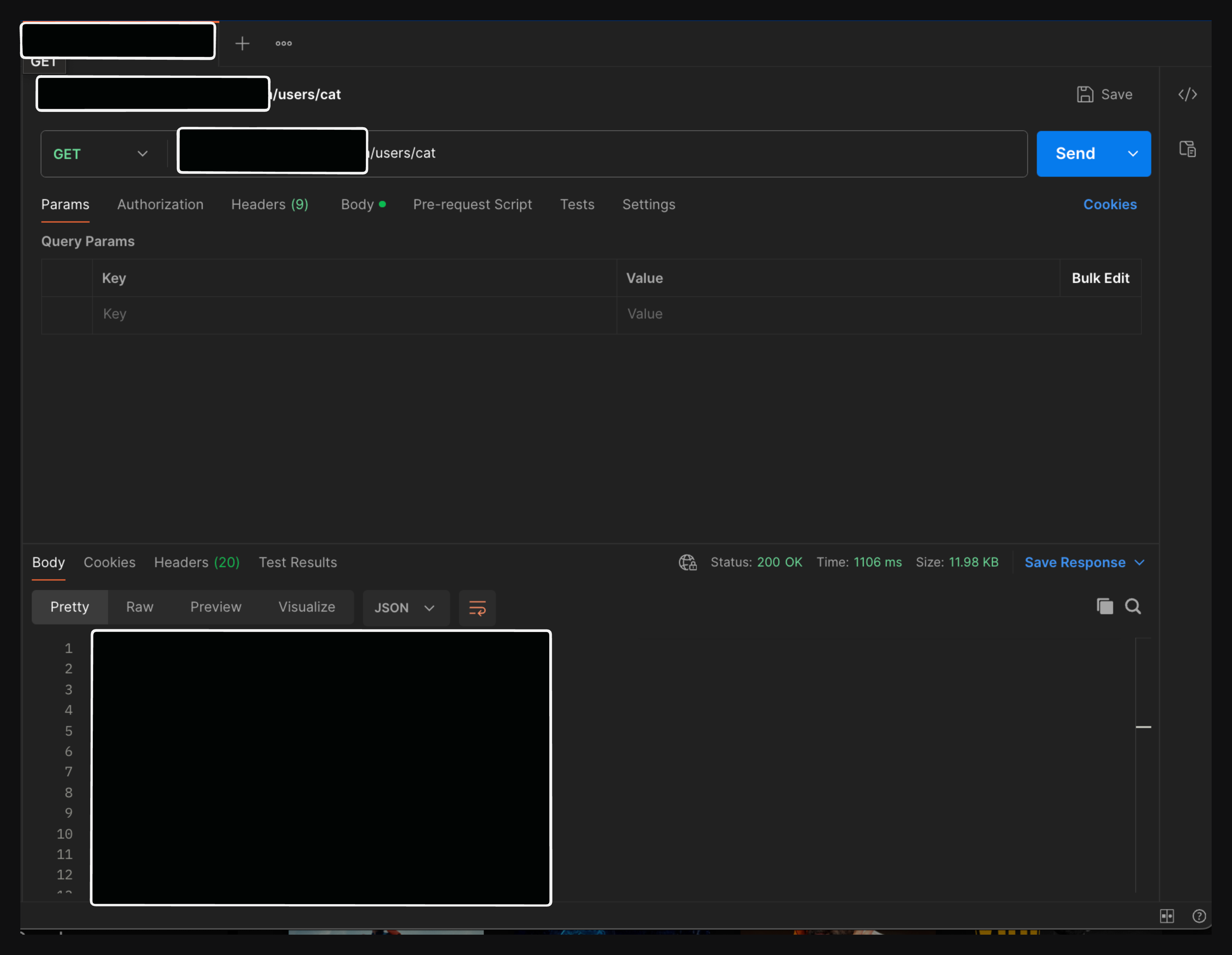
Sensitive Info
Then I started looking at their GCP API key because I knew that they also used Firebase because there were some errors related to it in the console (that's why sensitive errors shouldn't be logged on the client side), and after I used their GCP API key, I got their project ID and then tried querying their database, and sadly but happily, it was secure, and then I tried using their Maps API, which I was able to, and that meant someone could have exploited it.
UPDATE: After I published this blog, I again for some reason wanted to look at the code again to see if i missed something and I found more things
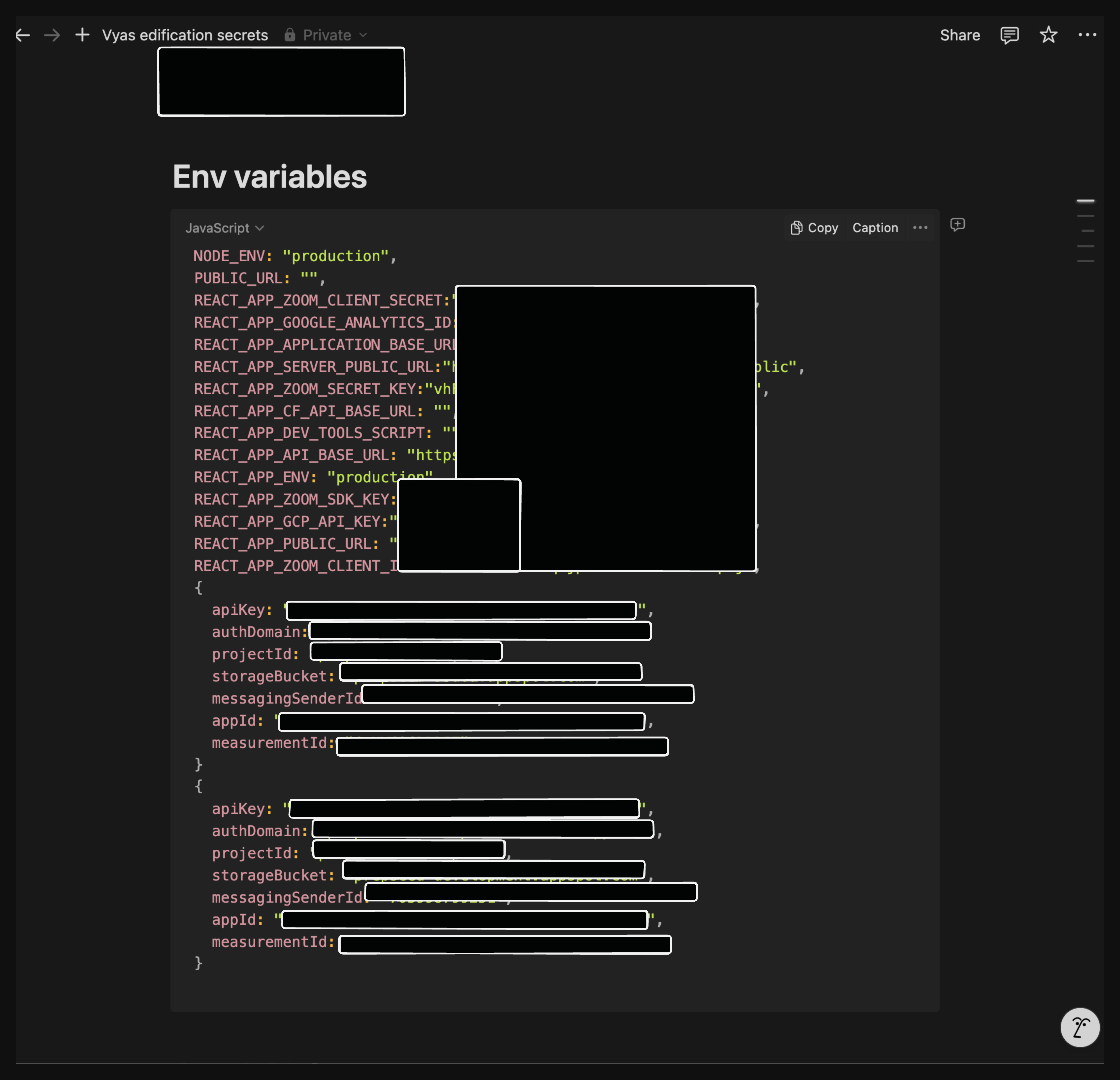
All Environment Variables
I also found that in their code there were a lot of mentions of "preleaf." I didn't know what it was, so I assumed it was a third-party service and didn't look much into it.
After finding all this, what I did was send an email to the company detailing all the things I found. It's been 12 days; they didn't even reply to my email.
So the things i ended up finding were:
- Environment variables
- Api keys
- Employee info
- Firebase project
2. Why shouldn't you expose this data
I mean, I don't have to explain about the employee info part, but I will explain about the other parts, so I'll start with the environment variables.
So environment variables are variables that are like these little (not little, tbh) strings of gibberish that are randomly generated and given to you by a third-party service, for example, Google, Zoom, etc. These environment variables are used to authenticate the requests you made to those third-party services, so if these variables are exposed, then some person can use them to impersonate you and make requests to the third party, and it will cost you too much, like in this case someone could have deleted their Firebase project and used the Zoom API keys to get into a meeting as a teacher, delete or schedule meetings like a teacher, or kick students out of the class.
API keys are just a kind of environment variable.
Firebase project ID, So I don't have to tell you all how unsafe Firebase is; like seriously, see this and this. These are just 2 examples of many about how misconfigured Firebase projects can be, and it's not just done by junior engineers; even senior engineers can do it.
3. How do you secure your systems
Environment variables
Don't hardcode them in your code, use .env.* files and use a library like dotenv to load them or maybe use a managed service, like the one provided by aws.
API keys
Use the same things as environment variables.
If you somehow leaked them, which can easily happen then there are options to rotate those secrets, do them immediately.
Firebase project
Don't use firebase please.
Conclusion
Thank you for taking the time to read this.